Introducing the BlackBerry Cylance AI Platform By Cylance Inc.
You'm extremely excited to speak with. All of you are wonderful silence. Customers we've been on a long journey together, the last what four or five six years now, and I'm extremely excited about this presentation, because it lets us know where we're headed together and by way of introduction for those of you haven't met me yet. I'm Scott, Sherman, Senior, Director of Global, Services, and I've, been here at silence for probably three years or so before that 17 years, supporting the DoD and intelligence communities, and I've really come to understand the vendor space in the last three years here at silence, in a way that I never anticipated before what I've really appreciated the most is aligning what we do to what you might call an organization's mission and that's exactly what we intend to support. In fact, our mission is to support every user and protect them every user under the Sun and every device under the Sun, and we'll talk about that more especially now that we are in blackberry silence which will conclude with at the end of this presentation, so without further ado. So yeah we've come a long way.
So we're going to talk about where we've been where we are and then where we are headed at the end, it'll kind of be like going on a rollercoaster ride at you know: Santa Cruz, where the biggest drop is kind of saved for the end and I can't wait to get you there. So as we go for this deck, what I really want you to get out of this one thing to walk away, at least, is the ability to message inside your organization's why you've partnered with an AI company called blackberry silence and what that means going forward and why and why it's so important to have done so, let's start in the news. So it's always great. To start with in the news, I would love to see a show of hands, but I can't, but I'd love to see a show of hands. How many people heard about the shadow hammer that was revealed yesterday in the news.
Basically, another supply chain attack much like CCleaner. That I know many of you I've had to deal with, and it's one of those by the Chinese Brian group. They go by a lot of other names as well, but they were the same ones likely behind CCleaner that that has just done this attack against Asus. The interesting thing about this is it's quite serious, because Asus themselves hosted the Malaysia just updater file for Asus laptops right, and it was hosted for about six months in between a half million, and a million folks have probably downloaded that backdoored installer on the racist laptops and then what we learned yesterday was that installer would go through and look for a set of MAC addresses. We know at least of 600, there's probably many, many more that are being targeted.
So it's a very targeted TAC, hosted by Asus official website, signed by an official Asus cert. The software was that was missing a date field and for those of analysts in the field, you will laugh at that and all lo and behold I mean it was predicted. If you are sorry, if you take this area screenshot here on the right, and you look at those hashes and some other IOC sir. But if you just look at the hashes, we ran those same binaries against our a model from two years ago, and we found that we predicted and blocked and prevented those from ever executing half of them two years ago, on the other half over a month before this campaign was discovered. So you just see this right here: okay, so yeah I'm reading the chat just to make sure other people are able to see this.
Okay I think I'm. Okay, let me know if I'm not, surely you can break in and let me know, but I'll keep going otherwise, and hopefully all of you guys can can can connect successfully. Okay, thank you! Surely so continuing on! So that's in the news. Locker Gorgas in the news. I, don't have a slide on that, but another one of those crazy attacks.
So much like I, don't know not pizza with some TTP's like Sam, and what we're seeing and a lot of these attacks, and we look at another factor like fin 5 that you know there's a lot of living off the land going on. But before we talk about living off the land, let's make one thing clear: you know show hands again how many people know about the miter attack framework. Well, everybody does because these days it's ubiquitous, it is literally kind of the new. You know Lockheed Martin kill chain. If you will, and if you look at the miter attack framework, you see all the thread actors there's about 78 or so of these apt known identified acting groups and one of there has highlighted in white.
That's barium, the folks behind the shadow hammer tech yesterday and all the other ones you recognize as well right, etc. , but all of them are still using malware right. So I just want us to realize that that malware still by enlarge the way. The vast, the vast majority of attacks still continue to hit the enterprise, and it's its. The industry tends to size things up by saying it's like malware versus file s or malware versus living off.
There's now vs. here. These attack kill chains usually involved a lot of both, and so we have to understand that as we go forward in this deck, and we'll look at an example of within five as well in terms of living off the land and phyla suspects as well. So one of the things in the past that silence is articulated that we focus on is our time advantage over the bad guys UL. So if you think about automation and speed on the part of the attacker there in red, because red is bad right on the vertical axis and then on the horizontal axis time itself- and you look at this line, it's kind of like that's how we've evolved as an industry, an information security, cybersecurity, now, whatever we kind of gone Lena lee, but the bad guys, of course, haven't waited around.
They tend to exponentially get faster, more automated, more stealthy. Their speed to compromise right is faster than our ability to detect, and so they've had this time advantage that pretty much represents the risk gap to your organization and your organization's mission. So what silence you know realize what Stewart, McClure, Orion and Cora are founders realizes. We need to approach this problem differently, give ourselves a time advantage and that's when you kind of see the Green Line Eclipse, the red line and from there on we have a predictive advantage powered by a narrow, predictive AI. That is now many months or years.
We have a slide in a moment that will express that advantage over the enemy and that's absolutely critical. As you talk about this kind of malware economy and the mobilization of malware, we really need to realize that we need to restore time to the defenders advantage and that's really what we've set out to do. We did some initial research a few years ago. It was actually one Sore Strider, the second one from the bottom first came out. It was during a black hat, I, think of 2016 or so and at the end of this report.
Now this at the time was the most advanced, prolific, sophistic type of apt attack ever using binary large objects using Lua programming language, if I remember, right, etc. , and at the end of this report, I think in the semantic report there's like 15 or so hashes of binaries and IO CS, and so we had an idea, let's run those against our old product because. You know what we've been doing this for a while. We say we have a predictive advantage, let's test it and Loki hold, we got all of those binaries and at the time we did this test. We got them 18 months before all Industry all of signature-based industry.
Any kind of human race technology whatsoever was able to even understand that this campaign had been underway, and so that 18 months, a window, if you will that time advantage was striking to us, since we did additional initial research- and here it is represented in terms of the number of months, were ahead of things. But if you look at like Z krypton, one of those remember 2016, Z krypton blew through like Microsoft Defender Ahmet and all these other kind of stacked. We had on the end point because it was so stealthy as a ransomware, but we had a six-month advantage before the first patient. Zero ever happened in the wild. If you think what that means over the enemy, the bad guys is.
We actually were pre inception before they even conceived of their malware campaign and ransomware campaign before they picked their crypto before they kept their schema before they did. There see ? before the any of their infrastructure chose a Bitcoin or not to use, etc. We were ahead of all that and sure enough. We actually uh s-see labs, a third party to test us against their. You know their repertoire of repository of the worst of the worst malware, and they found that across all that malware had an average of 25 months, predictive advantage over everything they throw apps and to us that was actually a Market over two years right.
So alright I think you guys get it, especially as customers, but I want us to maintain this momentum, because what we see in terms of how this affects our organization is represented by the next couple of slides that I'll build out your automation. If you think about the kill chain on the bottom, moving left to right as kill chains tend to do right. You have the malware economy, whatever happens there at some point, they try to execute malware. Then there's a call back, there's lateral movement, and it's some point to get your credentials and then there's data ex filtration at the back end right, genies out of the bottle. But let's look at like the amount of risk and work you can do before execution, there's not a lot, email filter and maybe some threat intelligence coming from the deep dark web on the main squatting using hacker reads, but really the bulk of the problem, the security problem.
If you go to RSA and you look around, and you're overwhelmed by blue lights, it's because this problem space, it's all the risk represented between primarily execution and credential part of the skill chain. It's the hardest part of doing the job, the lateral movement, although living off the land, all the PowerShell, all the command and control waves of occupation, everything that you know execution itself at anything. That's in the space is the hard work and also represents the risk to the organization, and if you get to credentials the genies out of the bottle by and large, we do hundreds of IR a year, hundreds thousands of compromised assessments, right, we've done and by and large once credentials are popped. The rest of the bad thing is going to happen, and you're not often able to get ahead of it. The genies out of the bottle.
So now, let's look at life with the predictive advantage right, and this is ends up being an analog with where we're going with our unified agent, we'll speak about at the end of the presentation. But really, if you think about what we've done there on the left is in blue AI has done the hard work ahead of time so that you don't have to we've done this prediction, pre execution, so that the endpoint finally gets quieted. Now, when I say, we've done the hard work I want you to realize. This is not some black magic. You know fancy math thing we did.
This is a very heavy lift. It's like forty thousand CPU cores. We spin up in AWS creating a tremendous amount of heat, doing this once or twice a year to create these new models, and you know we're looking at over a billion files and many hundreds of thousands of features across those files. If you look at the number of features you can extract from one PE, it's literally four point, eight times ten to the 344 power, put that in a calculator it comes back, and it literally reads out the word: infinity: try it on your laptop or phone, it's hilarious, but out of those you know all of that infinity. This feature said we're looking at 300 million features and in ways that humans don't even know how to look at those features to correlate and understand what the known universe of bad software actually is.
But we've done the work ahead of time and the point is in the middle, where there was a bunch of red, horizontal lines and risk now, there's only a signal, and that signal is what allows you and as an organization to finally lean full. It's literally, why you bought silence, why you are our partners, it's so that you can turn all these pain, points of alert fatigue and correlating and doing all the stuff up in the cloud after you've enriched it and vectorized it and everything else, and you know we also have a eye for optics to handle that middle section. But now it's a signal. It's not! It's, not a noisy massive cloud of work, and we'll talk about persona as well when it comes to compromise user accounts, but there are ways to apply AI to these key critical choke points in any kill chain, and so we turn these points of pain into what I like to call points of joy for the organization, the bottom right, positive ROI, how many security solutions in the world I've ever given you an actual positive return on investment right. So here we go.
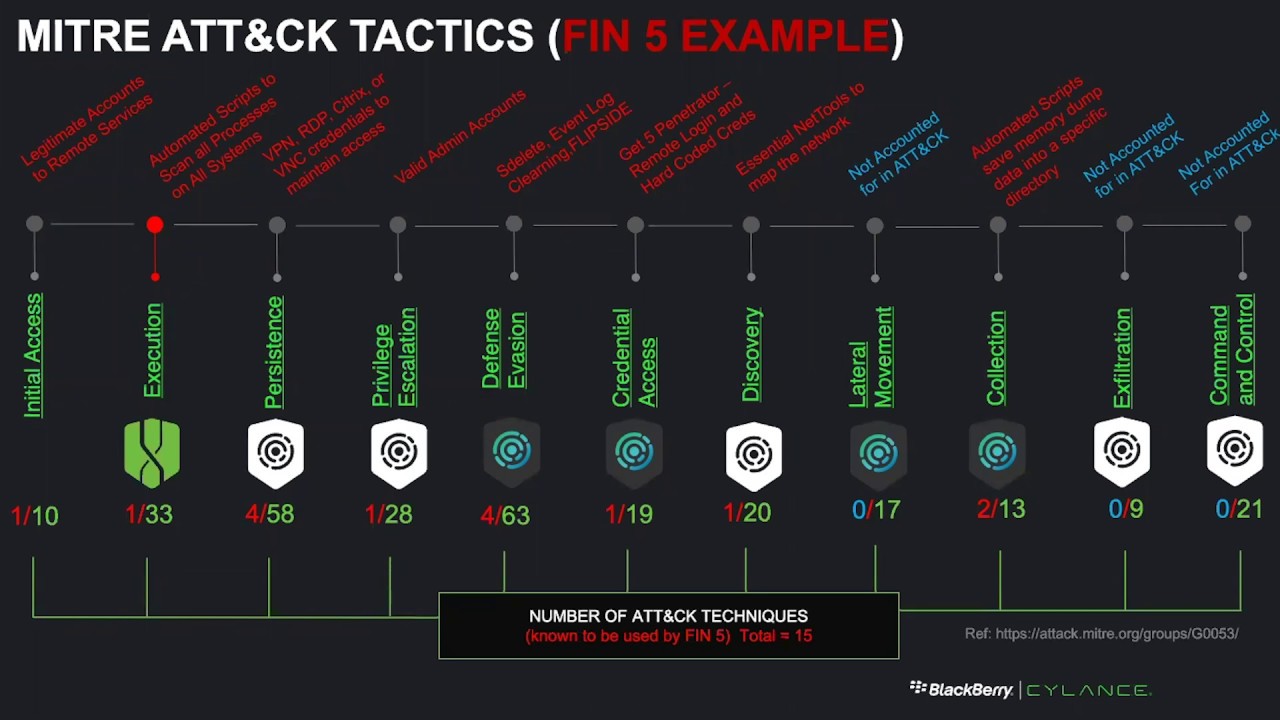
You get it right, so here is a legacy notional kill chain that you've probably seen me present in years past again, this is the linear version like a Lockheed, Martin, kill chain and execution sits right where it does on purpose. When we do our compromised assessments, the stuff there in the green again, it's that bulk area. So this is how we used to talk about things as industry, but the last three or four years right examples. We've actually seen the image to go towards the miter attack framework right. It's a much broader set across 11 areas of tactics, see initial access on the left.
It does kind of move left to right dish, but see two's over on the far right. For some reason, no matter underneath these giant categories of tactics, there are those numbers which are the set of techniques that we as an industry, have contributed to the miter connect framework and may have extracted and say these are the ways we know the bad apt groups, like those 78 groups. We saw in the beginning of this deck know how to do things underneath these tactic categories right. So this is like the world of miter attack through a lens I will continue to lose use this lens, as we build out. Of course, I have another deck that goes for an hour right talk about all the TTP's and all the tactics I should say associated with these.
Are these tactics and the ones in white or ones that you recognize right off? The bat is giving you problems right, causing you pain, Emily at all, but one of the things that's common about all of these tactics today is that they're all seem to be moving at what you might call the speed of computing, their automated their scripted out there, the ex filtration or the destruction can happen almost automatically the second. You know a button hit across the Sam environment or my clock or Gaga there's so much going on right now. That's moving so fast that, if you're not addressing it or able to address it at the endpoint and if you're, relating, if you're, waiting on the cloud to do the correlation for you to tell you something bad has happened, but the ad at the end and past tense. It's going to be too late for you for some of these fast-moving destructive worms, for example. So we'll look at this, and we'll use fin v right.
Anybody, financial on the call, will recognize these guys right and right away: they're the folks behind Raw point-of-sale Raw POS software targeting carding data on POS endpoints. Of course, these guys have been around 10 years, killing it um one of the reasons they're killing. It is they're not using zero dates. They're not using remote, exploits like you turn on blue and anything else that comes up struts, et cetera, they're, not using spearfishing, which we still say. A vast majority of text normally use instead they're hiding out an easy land, they're literally using all the credential dumps that have been taking place over the last several years that are constantly ahead of our password policies and our ability to manage those identities and the mean actually pause.
There. There's over 10 billion records out there of our username passwords, there's only like 6 or 7 billion people, the last time I checked on earth. Do we have a problem with passwords our passwords dead? Yes, passwords are dead, but from a bad guys perspective like 10 5 long live passwords because they are using them to get into RDP they're popping them. They were using working with via POS vendors subversively to obtain those password lists to go right into the organization anyway. So you get the idea of what fin 5 is about and how they kind of live off the land and use crews rather than you know, malware and all the other things right.
So they do use malware raw POS, but that happens at the end of their kill chain right, see how it goes, so minor attack covers a lot of what they do, but not all of their TTP's. We know because we've dealt with these guys in our IR s, a ton. This is a screenshot of the tools that mite text says that they use, and it's its completely accurate. It might not be the whole set, but it's its true and what you get out of this is basically these guys are using legitimate stone. Crews, like we talked about, and they're largely using living off the land or law file, this type of attacks, we won't go into the industry jargon around what we mean by file lists usually file.
This actually does include a file in PowerShell or writing to the mention writing to disk or something like that. But we won't go into that will just describe these guys is basically living off the land and for our purposes, that's what we mean by finalists right, and you go across all these different tactics that they used. You know eternal emote services, credential dumping, redundant access right, so I'm going to map out across the top. Those tactics that these guys are known to use and the ones in blue there at the end are ones that might our attack doesn't account for so everything you see here: I pulled from I, dare attack and just plopped into the same lens that we've been looking at and if you look across the bottom, you see there's about 15 different individual techniques under those respective tactics and whole that we as a human race and industry, understand about fin fire and so now, as silence customers, you're saying, okay, cool, show me how you guys address this. Show me your coverage right, because the industry's coming at you hard, post, RSA, there's a lot of third-party testing, saying show me your miter attack coverage and I have air quotes around the word coverage, and before I show.
You realize something about this and look well message more about this in the future, for your benefit, if you have an organization or a software solution that has let's say 100 percent coverage minor attack, you should really scratch your head and ask yourself what does that actually mean, because we just saw there are 78 user groups across 200 different techniques and the methods of those techniques, the sub techniques, if you will and minor attack tests, might just take for one registry persistence setting, but there are five other ones, and if you just get that one, you get a checkbox, and you have now minor coverage underneath that method of persistence, and you're, good, and you're moving on. So it's easy for anybody to get full coverage per se. But do you actually have full coverage? Is a vendor. It's an empty statement. It literally doesn't mean anything, there's no framework on earth that keeps up with the entire landscape of all the threat actors over the last twenty years altogether with emphasis.
So that said, let's go back to how silence would stop this right, so obviously execution the raw POS malware itself, predictive, pre, execution prevention. That's the silence, protect shield. Then you have silence optics right. These color shields. These shields would indicate to you where, in with silence optics, we would be able to detect, and even if you wanted, to block those types of actions of living off the land, moving around collecting data on gaining credential, asset access or excavating, privilege, etc.
, right and then the white optic shields. Are there just to show you that we also have the ability to detect any number of these other things that happen. Maybe you don't block because of there's like physics, reasons why you wouldn't want to block certain things without vetting them. First, this kind of things right, so you're kind of your classic DR of after the fact. We can do that too, like everybody else, but really focus on the fact that you have this dream symbol left and the four colored in optic shields.
That say, you know what I can have enough intelligence on the endpoint to understand when bad things are happening and interject. This kill chain at the same machine speed that these guys are trying to move or attack, speed that they're trying to move and get ahead of them so that they never get to the raw POS part of their kill chain. They never get the pole carding data, let alone exfiltrated right. This is the goal of what we're trying to do in the industries. Get ahead shift left all the words, but here you see how we kind of map to it.
Okay, this slide is on purpose and eyesore, but I want you to realize if you were to only do things after the fact up in the cloud in your sim after the fact and enrich it and then understand all your events and pivot and correlate and hunch and figure out what happens, root cause by manually pivoting as an analyst you'd end up with a story. That's kind of like this, based on one of the lab demos, we did around fin 5 right, one of our own kind of we create what they might do things, and all of these things are things that an expert needs to look out. Vet make sure our class positives correlate put together, timeline extra, but wouldn't it be nice if you could just prevent this stuff from happening at the same speed that the attack happens and interject meaningfully, so I want this slide to be an ice, because I want to get rid of this eyesore in your lives. So we throw this slide away, and we say no we'll get early on enough in the kill chain. When we replay this, it took us about 45 seconds to move laterally just by living off the land right I have a demo from a past talk, I did like huh.
We talked about dwell time in industry, going from 400 days down to like less than a hundred date, and we're supposed to be happy as human beings know 45 seconds I think Stuart and Brian Rum son are doing demos now, where it's like five seconds, they've already moved laterally the automated scripts right so yeah. So we want to get rid of this noise for you and that's the whole point. Okay, so some things bad things do happen and one of the things that you guys have as optics customers now is this amazing tool said it's a Swiss, Army knife. It sits there underneath at the endpoint right taking up very little resources, but when you need it, it's there for you, it can push or pull any kind of software or data. You want to you from the endpoint.
It's its quite amazing. You want to call forensics package absolutely do that if you have third-party applications, you need to push in the face of something like a want to cry attack. If you have a workaround that will Ravenna worm from from from spreading, if you just change it and flip a bit in the registry, we can do that if you want to apply patches like MSO and seven, because you turn a blue or so you turn a blue is trying to spread through your network with double pulsars warming technology. Let's do that because you can now a silence optics right and better yet at the end, and we'll save this a little. But you know we have these play books that you can orchestrate in your environment, because you know your environment.
You know your workflows right. If you don't, our services will help you do that, but you can automate this now and so, let's get rid of all the heavy lift that a human has to do all the time. If we know that we know with super high confidence coming from the endpoint, that a bad thing is happening, let's automate those playbooks pull those packages make those changes whatever we need to do. It's a hugely powerful tool and I. Think you guys, as a user community, are on fire about the automated playbook aspect of optics these days and the other thing with optics is it's.
You know it's got this amazing API right so via API. Now you don't even have to go to the console. You can request it and it's a query. You can look at a focus view and get to root, cause analysis. Furthermore, you can publish an update, even delete your context.
Engine rules exceptions create I'm reading off the slide, because there's a lot of cool stuff, you can do that's the whole point. Service lockdown commands to endpoints retrieve arbitrary files from endpoints doesn't sound like much to say arbitrary files, but that's the universe of files on your endpoints. You probably need the poll when bad things are happy. You can finally do that now via API, okay, so I'm super happy. We gave this to you because you were clamoring for it, and I'm super glad it's in your hands.
We see success with this all the day in the field every day when we do services around optics, it's amazing syslog. Another thing you can. Obviously, if your RSA, you saw somebody from Splunk present at our booth, and they were talking about how with syslog. Now it's so great, because you could pull our context analysis engine feeds directly into Splunk right. You can automate all the workflows for receiving that you can triage right away.
You want to triage off of silence intelligence, whether it's a malware detection with a high confidence, because AI says it's high competence or it's a high confidence that content context analysis engine hit anything that's high. Confidence is high. Fidelity coming from your endpoint is solid gold in Splunk land, and you know this better than I do but just realize this is all now syslog happy. So you get the stuff right away. You're, pivoting right away! You all are you already know where to start in terms of triage and priority? And then this is a slide.
That's visually! I! Think it's an awesome graphic by the way. Whoever did this, but this visually gives you a wonderful look into the different areas where we have. This alliance called axiom that we work off that continues to grow even beyond the logos that you see here, which are all wonderful everything from demister, ass or logarithm, just explode. Obviously, our friends at masc, a psychotic bit class and for Cosby I mean this around the circle. You see some high quality of folks that we're fully integrated with now, and then I source like to say, there's much more, and we can talk to you about it.
Okay, so I got to the frame. My favorite part of the whole thing right, I told you we're going on a roller coaster. Now it's time to clean, clean click. Talking that's time to go down, and hopefully we're keeping up with my pace is like we said we have a lot to cover, so we've built this thing, and we've been hard at work at it, probably 18, 20 months now or so, and we've built this thing. That's a silence, AI platform.
Now every vendor says they have a platform, we get it, but this is new. This is an AI platform. This isn't a native AI agent sitting on all of your endpoints, using shared resources and microservices. Architecture I will go through this in a moment, but it's its new because it gets you it is future-proof. This is giving us set up to use math and machine learning and an is going forward off of the end point where it matters, because the end point is still the Nexus of the problem, whether it's an identity problem, an ex filtration problem, a user problem, obviously malicious actors doing stuff problem, malicious insiders' problem.
It all still happens at the end point, so we built this agent to live where it matters, and we built these agents that we can hot plug in new machine learning models to help us solve things with high fidelity, high confidence in the future. This is why you're still partnered with silence, because you know we can bring this to you. If you look at this platform and kind of from this perspective here, you see that it's its all about the outer ring everything we do here, as you already know, is about prevention. It's not just predicting malware, pre execution, it's also focusing Nutella just down to let's say optics where we know we can make decisions in real time and automate things like play, books and responses to interject the kill, ting and shift left to stop it before the bad thing actually happens meaningfully without the cloud without sending your private data, your privacy or your GDP. Our worry data up to the cloud exception right, and you'll, see us do this in the future looking product as well towards the end of the deck I'm about to get you I'm, so excited about.
So everything sounding. So as we push down to the intelligence down to the local device, I try not to push things up. We don't need, because that's bad for privacy, etc. We have the ability to focus data science where it needs to be, and this enables our axiom aligns that we just saw to actually use us meaningfully. This enables our OEM products to actually use a very lightweight integrated, shared services' agent on their respective OEM endpoints.
If you will in a wonderful way and also future fuse them to do math on their OEM devices. This is literally where we built the endpoint features. What I'm trying to say if I haven't said it loud enough. There are many benefits to this right features benefits going on here. Some benefits.
It's a single agent like I, said it's locally, I, there's no latency by latency. We mean you, don't need to worry about the overhead, be off the processing of the cloud to get your intelligence right. So much of what people are building now is because they can. So you throw everything up to the cloud, even your IOT down here, flowing up to the cloud without even filtering at the end point: first: okay, you're, throwing all this stuff. I got all these conferences, and we're doing so much the cloud, but we don't even know why necessary we're doing or what information should be up there, because we just sent it all up, and now we're trying to get smart in the cloud.
So silence is doing good, apps away we're sending down models and intelligence down to the endpoint where we need to be without the latency, so we can get ahead of that thing. Automated DR, like we talked about with play books the ability to anticipate what the bad guys going to do next and stop them before they get there and this powerful API we're talking about now. We'll talk through just a few of the actual, discreet features that I know you're on pins and needles about some of you at are say, I've seen some of these before maybe, if you're a prevention con, you got a preview of this, but this is what it's gonna look like right, not not the photo but to the left for a second. So one of the cool things about what silence is able to do now is give you better classification that has more context around it. So as users you're familiar with like malware versus pup and silence, stop something from executing, and you're super happy about that.
For obvious good reasons, you still kind of want to know why? What is this thing? Is it awful? Was that a worm we just stopped and prevented because wouldn't be nice to walk into the board and say: look you know that AI thing I bought two years ago. It's still working at its stopping worms, so we want to give back to you some enrichment around what we're doing with our AI, so that you can message internally and understand what we're doing and make better decisions, as analysts either side about that in a moment, but so we're also introducing what we call risk levels. So you know how to triage better and our taxonomy, which you do see you there in the photos, is represented in the photo. I. Don't know if it'll appear exactly like that, but we'll show you like what this is.
Very similar to things that are in want to cry: it's also known to have ransom component, and it's wormy, or it's using an embedded portable executable, or it's got aspects of quack, baa and SFX, oh by the way, and it's using this, maybe it's being packed or something. So you see how you can kind of make quick decisions, and this kind of cascading taxonomy that we've figured out. We've cooked this toast this out of our AI and that's what's so exciting. All right now is starting to tell us back as a vendor, even let alone you as customers, why it's making the since it's making, so you can be better analysts, okay role, based access control, focused, you know, send around like need-to-know concept based on job functions with much more granularity. You all been asking for that.
We've delivered additional memory, forensic protections and won't go into the details of those, but doppelg?ngers like when a process is trying to write and write for, writes to disk it gets interjected and duplicated and and and then used for malice child processes where the parents modified the memory permissions, that's a bad thing. Well, we all stop that now: protection from one process modifying something adjacent, not the parent, but something adjacent that I didn't even own. We got that right. So this is new memory, defense protections, keeping up the threat landscape, scalable drooping- this is huge. It goes boils down to like tags.
We want to be able to scale the grouping. That's always been a challenge for every vendor, including us. So now we have a way to do this. We have a way to assign multiple tags or labels. If you will to each kind of thing, a group or thing rather and then group make groups out of combinations of those tags and then also filter based on those tags.
You get quicker resolution and pivoting through the dashboards. You know what you're looking at script control we've been great against PowerShell, one-liners two liners exception. We want to keep up with that landscape. I mean every week, there's probably five or six different ways to misuse: PowerShell and live off the land. We will continue to keep up with that.
We have some new stuff that we're releasing with this unified agent coming out and obviously whitelisting guys have been all been asking to be able to do this by current process. Okay, we got you and some new controls around that. So these are the features right. I've, dead benefits and features. Did the Kirby vacuum thing so here, so now we have my favorite part, so we are an AI company, as you guys all know right.
We are now maturing that machine learning model. Oh, we have been over the last, whatever six or seven iterations, of our own internal kind of generations of models. If you will, but beyond that you can't, when you build in AI, you don't just get to go from step, one on the left and get to step five, no matter how much money time. Sorry a data, scientists and technology throw at it, you have to evolve your AI. We started doing this in 2012 when we're at step, one right, classifying things and understanding how to predict things.
Training in the cloud like almost everybody else is doing still as well step. Three, you know enhancing our models. Getting larger feature sets, like three million features, sets or in a billion sorry a billion samples, but let's focus on step five, because that's where things get interesting, if some of you follow like the field of AI in general, right, more abstracted darker describes these three waves of AI that will come upon us as a human race describe categorize and explain when we went the AI to get us better as humans, we have to ask it to explain itself. We have to remove some of the veil that normally might happen in an unsupervised kind of type of model of training, and we do supervise and unsupervised. We do many methods inside what we do when we build modeling, but just in certain areas.
Furthermore, we want to know why it makes the decision made. In our case, of course, why is this malware actually considered malware? Why should I believe you AI right? So we're we're giving back to the analyst, and the other thing is we're going to give you some interpret insights that are meaningful to you. As an analyst, you actually make real-time decisions in the face of the threat and then the robustness aspect is interesting as well. You read about adversarial machine learning being able to mess with vendors that are using like basic machine learning, automation and by and large, that's true. The field of machine adversarial, machine learning is actually accelerating very quickly, but we're so far along and are a've been doing this so long years before the rest of the industry, and I'm fully on a soapbox right now and proud of it but proud of our data science team.
But really we have so much robustness in this model because of complexity because of different angles. Because of how we're looking at things, because also our data science team spends a lot of time trying to break our data science. They come. They have the right pedigree to know how to break and do adversarial, machine learning and other tactics to break us. So we're we're breaking ourselves always, and we're out of state of robustness.
Now we're we're very happy, let's put it that way. So so so right we have this thing right. It's we talked about explainable AI, we're fast approaching as an industry. The need to have new metrics right, so we need to be able to have a predictive advantage metric. That says the number of days that your predictive AI, whoever you are as a vendor, is able to anticipate and predict the problem it's designed to solve right.
So we want to start measuring that Y so that we know for getting better against the overall broad anniversary space. We know if the, if the cushion of time advantage that we have is getting shorter or longer. In our case we know it's getting longer. We still have models from October 2015, getting today's most advanced malware out of the box without any connection of the cloud. Let's start measuring that okay, as an industry, let's start measuring to how long it takes an analyst to make an informed decision based on the ability to have intelligence, local in the system and inform that analyst.
So you want to make a decision based on confidence. So do you have enough confidence to make a decision fast enough to make a difference? That is the metric. We need to start working for now whether that decision is an automated decision or a human decision break that out and start measuring that as a sock or as an analyst as an organization. So the next thing- okay, so this gets us to where an example of where we're going and if you were at RSA, you probably saw a preview of this where he actually got to step up to keyboard and demo it even so yes I'm speaking about persona non getting there. So look.
We have this fully extensible thing: we've built with full API access. It's built on a microservices' architecture, so allows us to hot plug and pull plug in and plug out different machine learning models, different types of feature sets etc. without requiring an agent update right. So we've built this AI platform that we can its future-proof by definition, by how it's designed and then also we have an agent that has optics functionality. You can do anything it needs to do on the agent, so never mind can I am.
We have you covered. You can do all the things you need to do right. You can push whatever you need to push-pull what you need to pull. Get things done so now, if you have like an, ABA project you've had this you ABA project, going on for 18 months or two years now you have the intelligence, that's meaningful about whatever insiders or this or that about coming out of your VA. But can you take an action meaningfully on the endpoint from that new idea? Intelligence Platform you've built well.
Let's do that now! That's what this API structures for right so allow us to be the actuary to get things done on the endpoint, based on your axiom, based on your other technologies that you're pushing from so here, I go. Take a breath and say I'd like to introduce to your silence, persona best represents, in my mind, right in our mind where we're headed and why we're headed there right it's its an AI driven behavior and biometrics analysis engine and that's a lot of crazy words. And as you read them, you still don't know what it is. But let me describe it differently. I came from a DoD field right and the idea that I can authenticate a person at a point in time and know that they're that person throughout time is a challenge the DoD never has solved.
To this day we have PKI, we have high confidence. We have the ability to revoke a cert. We have trust built in, but it's all still happening at point in time aspects right, so you can steal a username password and even a PKI session, because the user is authenticating for you inserting a cap card right. But let's see what happens when we have to answer the question. How do I do this over time continuously? How do I dress this password problem when there's a 10 billion records out there and all of our passwords are effectively dead? How do I just problems like most people are employing two-factor authentication over SMS, which is entirely broken for any kind of meaningful operation where you need mission cadence? How do I address these problems? Well, this is what we're building sounds persona, so um benefits cont slide right, so top left, its AI driven its biometrics, so it knows who you are based on, how you move and the other aspects of like how your arm articulates when it's using a mouse, the distance between keys and how your fingers hit keystrokes the cadence, the pressure, all this kind of aspects of typing on a keyboard, its uses, biometrics or in terms of how you, as a user, interact with your machine.
Do I right-click and paste, or do I, do CTRL V or this kind of things? How do I get around normally as a user when I first log on right, um and all of this kind of things come together to create this metamodel, even Windows events and network stuff, going on all these micro models create a metamodel, a combined model that gives you a trust score, and this trust score in the middle is front and center. For a reason, it's a signal that you finally have that the human being at the keyboard is the human being. You think it is, and that's paramount and from a number of different angles, of course, insider threat, audit, who is at the keyboard after the fact when you share using human passwords and like DoD or like oil rig environments, where you know your users are sharing log on indications, wouldn't still nice to know whether it was Bob or sue that was at the keyboard when the big button was hit from on a perspective. There's so many other aspects this, but my kill chain, our user level processes or those things are getting interacted to it's. When we open up Excel with a nice acute IQ file.
That runs something like botnet and inside the application, all botnet it's happening in a user level process right I want to know when that process is not the thing, I thought it was right. So this is what we're building. So we, you got a continuous user trust there on the far right, which is the continuous off kind of aspect, I'm speaking to the whole time, it's giving you real-time alerts, so you know right after bob has become sue, you'll start to learn that pretty darn quickly and that's a signal. That's your red hearing, a canary in a coal mine that says, I have an identity challenge on this. Endpoint now should I take an action with optics or now should I feed my UI BA or now should I step up off you and force you to put in a CAPTCHA or to use a duo, authentication token to prove that you're still Bob right, because I don't think you are any more right, and this is all happening locally on the Box.
This is not happening later with your personal information. That's very private upping the cloud. This is happening via locally unsupervised models on the box, so this is new new new, and I know. The vast majority were nodding, your heads and are salivating like I am, so it's also important when it comes to privacy, and I've been hinting on that, but raw data is not leaving your device. Biometric data is not streaming upwards.
Models are trained and scored locally on the device and the device. The data is not stored up in the cloud so from a privacy perspective. Everything silence does, and I ate tribute dishonestly a lot to one of my mentors Malcolm Hawkins who's, one of the most wonderful speakers around privacy I, know and provides a lot of thought, leadership and guidance to our company and our mission. What we're creating everything we do? We don't like to send up to the cloud- and this is very much unlike the rest of Industry all right, so I've said a lot about persona. You can tell I'm excited I hope you are as well we'll be able to reach out to you more about that as it gets further put into the product and released and there's you know, persona is something that it will exist in a certain way in the product right, largely solving the stolen password credential problem in the kill chain, which is very much on point for today's security landscape, but it can be and well be, and should be so much more as we go forward, and we need you, as our customers and our in our customer base as partners to inform us.
How could something like persona fits into your three-year identity plan that you're starting to build out your 18-month identity plan or your you a BS a your integration, whatever it is, let us inform us, so we can mold this to be what it needs to be, which is a high competence signal that the human being is the human being the whole time all right. So we are silence. Blackberry, I, look at the time here. I got about 10 minutes left, so I love. This slide, because it's its these two wonderful shields that we both have had for our existence.
I use the BlackBerry for my entire career in the DoD. A lot of you are nodding. Your heads, I love, my blackberry. Take it away from my dead hands right so, but blackberry now is obviously so much more, and actually it's much less to do with anything to do with manufacturing of handsets right. So they are building this mobile UEM and they all they built it, and they're building the future of what that means.
They're also focused on things like automotive sector, in a really, really big way. I think the news just from a couple of weeks ago, if I remember, right, I, think the Canadian government offered 40 million dollars for blackberry to help solve the autonomous vehicle problem space for Canada and the West is here we are- and this has to do with things like vehicle infrastructure, vehicle-to-vehicle vehicle to internet right vehicle to XOR things around the vehicle, so that vehicles can have that again local intelligence to make decisions. You don't want your car to have to go to the cloud before to notice. If you put on the brakes, you need local intelligence and so BlackBerry's building this out now, as you look at these two shields for those of you on the call that are in the automotive space that and already know this about us, we have a phenomenal pedigree in automotive insecurity, everything from production security and incident response to vehicle security, to worrying about Candice learning, about the entire telematics platform, learning about the backend transport of over-the-air, a kind of transport certificate and there's not anything in this space, really that we haven't at least touched and have a degree of expertise on, and so, when you put these two together now you have this thing that allows silences skills to expand an influence, BlackBerry's platform that they're building and Blackberry are already in 120 million vehicles. They own Q, an X, Q and X is one of the most trusted aides, absolutely the most trusted and secure embedded system.
For this application there is- and it's not just in just the car. You know the top tier cars. Isn't a lot of the supply chain as well, and so blackberry also have other things they have. They have something called Jarvis which looks at binaries and Ben de binary's, etc. , and breaks them out and analyzes them and looks for vulnerabilities and looks for coding system, including flaws.
Something like this perfect application for supply chain. Right. Blackberry is doing so many things that you may or may not be aware of, because they haven't always firmly planted themselves in the quote: unquote cybersecurity industry. But if you went to RSA and you looked at our booth, you saw blackberry, silence and big letters, because their full intention is to completely help us carry out the mission and actually protect our mission, which is to protect all the things under the Sun, not just the people, but the things. So this also applies to Internet of Things.
This implies to OEM and embedded solutions, and again this is obviously not just anything new with malware. This is all the AI. This is as devices streamed to the cloud. Can we start filtering some of that data before it goes to the cloud? Can you apply? Algorithms locally to help bake better decisions at the edge, much like we do in cybersecurity, but now for autonomous vehicles or robotics or other things right. Blackberry has a huge pedigree in health care that everybody probably does know about, and many of you on the call also know we have a huge pedigree with healthcare, especially in the way of services.
We have gentlemen, like Rob Bathurst, who came from Mayo Clinic, who is one of the most knowledgeable folks that would be noted, Hind's, and that kind of thing that guides a group of consultants that are phenomenal at breaking anything to do with medical devices and patient operational environments or entire facilities from top-down governance, all the way down to device level security. So we have a huge pedigree as well so looking forward, what does this mean for you across any industry you're in? At the end of the day, you have the most successful AI company in this space and a massively powerful blackberry with ties to government to all the g7 governments, I think and one of the few vendors that can claim that they're highly trusted. They understand security in their DNA, and you're, combining these two forces together in highly complementary ways with very little redundancy and take my word for it. We've just been merged, and they are letting silence stay as an independent business unit subsidiary, so that we can keep doing exactly what we're doing for success, but leverage all of BlackBerry's infrastructure, all blackberry, strengths, all of BlackBerry's connections and all of BlackBerry's wisdom and knowledge around things like automotive and mobile right. So how can this not be one of the most beautiful marriages ever as we approach an era of AI Renaissance, an era of 5g with Internet of Things, and even your power meter at your house, streaming 5g to the cloud there's so much geopolitically, even going on that make this the right? Marriage at the right time and I wish I could stand on a soapbox and scream, and I'll have my lungs.
This is the right marriage at the right time for all of us. This is what needs to happen because who else is building a native AI platform agent on the endpoint that very hard to do, and we've done it we're bringing it to you, and we're extremely humbled and proud that you guys are our customer base that we're on 117 million in points now that we can do things with data and data science that we've never been able to do before, because, like this marriage, the future is absolutely wonderful. So please stay with us. I have a few more slides, I'm going to hand off to summer again. Some are you ready to speak to these I sure AM? Thank you.
Take it away. Thank you. So much I again, I just wanted to run through just a couple of important things to take away. I want to reiterate that you can always go to silence, comm resources, user groups, and you can take a look at when our upcoming user groups are and where you can join in, and they're, really, really fun, and we'd love to see you at one. You can email user groups at silence, comm if you'd like to host or speak or even just to get more information about what we have coming down the pipeline there, and we're happy to answer that for you.
Oh, I deserve the next one Thanks, just a couple of resources to keep in mind, and we'll e-mail this out to you in our post event. You know you can go to the support community at any time and support silence, calm or through your console, and you can post your questions there. You can engage in discussions with our support staff and other users, and you can ask for assistance or logged a ticket there to tech support if you need to we're always online, so you can also and I highly, encourage you if you haven't already stay current with the latest cybersecurity news and check out our award-winning blog at threat, vector dot, silence, comm, it really is fantastic, and it's you'll spend all day on there. If you, if you really get into it, the blogs are fantastic. If you have questions or need information specific to your account, please go ahead and reach out to your account executive or your technology business partner.
We will be answering questions after this webinar again, but it's something very specific to your environment. That's the best resource to reach out to, but you can also contact for general and firm about the company or just questions in general. You can call eight four silence, or you can email sales at silence, comm for the next steps again, I want to reiterate: there's going to be an email coming that has a survey in it. We really need your feedback so that we can make sure that we did that we deliver the value to you in these future webinars we're going to try to have them once a month. For you tomorrow is the silence person tagging exposed bypassing next-gen webinar.
You still have time to reserve a seat. They are really, really fun. I, really highly, recommend it and be sure to save the date. We're going to do this again on April 24th at 8 a. m.
Pacific time and I really hope that you can make it. Thank you all so much for attending we'll talk to you again soon.
Source : Cylance Inc.